Proxy servers were originally created to protect private networks from being exposed on the Internet. But a proxy can be used for more than only internal networks— it can be used to protect your identity, limiting Internet usage, monitor it, circumventing geo-restricted content, bypass firewalls, SEO audits, web scraping— and many more.
In this guide, we’ll go into detail about the 10 ways you can efficiently use a proxy server.
What is a Proxy Server?
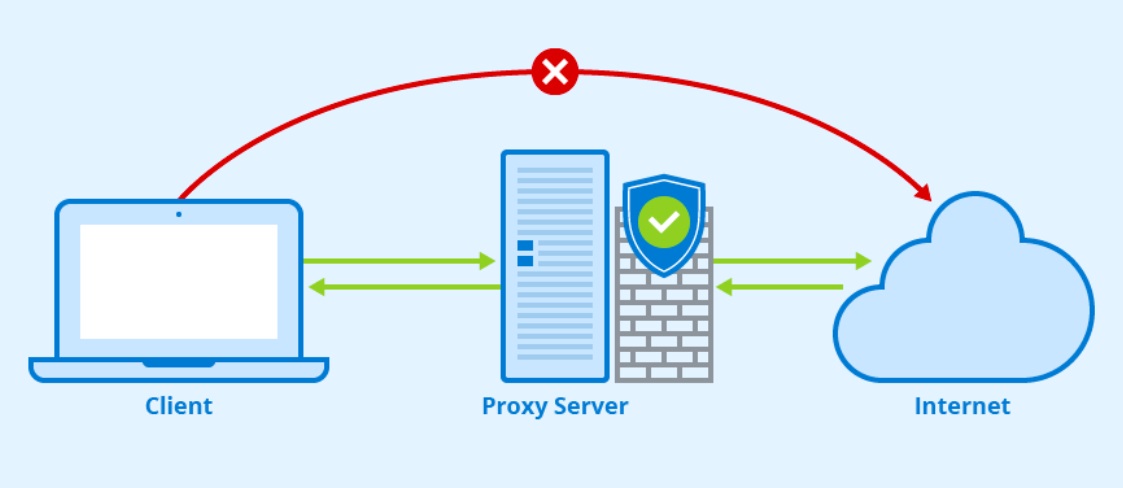
Proxy servers were initially designed to protect internal networks from the external world (or the Internet). Proxies are configured as the gateways to the Internet. All clients inside a local network that want to access the Internet must first go through the proxy. In the same case, all external communications from the Internet wanting to access the internal network must first go through the Proxy server.
There are three benefits to this:
- Access to the Internet from internal networks can be monitored and limited.
- Proxies obscure the origins of a real source. From the face of the Internet, it is the proxy doing all the requests.
- Threats and attacks from the Internet face the proxy, which acts as the first line of defense— filter or firewall.
Think about a proxy as an intermediary. For example, you can hire an intermediary (broker) to deal with all international negotiations (Internet). The intermediary is the link between you and another group of international people. This intermediary is essential because, first… it is someone you can trust; they channel what you need and filter out nasty comments, bad deals, etc. They use their face/name (not yours), so if something goes wrong, their reputation will be affected (not yours).
As shown in the picture above, a client inside a local network and behind a proxy server, can’t access the Internet without first going through the Proxy. All communications between an internal network (client) and the Internet MUST always go through the Proxy Server.
NOTE: Proxies are not the same as VPNs. A proxy server is the gateway, a VPN on the other hand is an extension of a local network into another geographical area using an end-to-end encrypted tunnel.
Ten Ways to Use a Proxy.
As mentioned earlier, a proxy forwards the client’s requests as if they originated and destined by/to the Proxy. A client hires the “intermediary” to do the job, so the client’s true identity is hidden.
So why would you need the proxy server in the first place?
1. It Hides your Internal Network Information.
When you connect to the Internet, you remain anonymous by hiding behind the proxy. The proxy works on your behalf and uses its IP information. The proxy takes over the request you originated for a website (or server like torrenting or streaming) on the Internet. So the destination receives the request from the proxy, not from you (the end-user). This automatically creates a new layer of anonymity in all your online activities.
2. Circumvent Geo-restrictions and Censorship.
By connecting to a proxy located in a specific country, you can access the content tailored from that particular region or country. The target service (a website, streaming, news, or search engine, etc.) has no idea that a user in another country was the one that generated the incoming request. For a server, a proxy looks like an ordinary user (unless its IP is blacklisted) . A proxy is a way into other regions’ content and, at the same time, a way out of censorship.
3. It Acts as a First Line of Defense.
A proxy is a face to the Internet so, it may be used as a firewall and data filtering application. Hackers or any external threat have no way of targeting end-users within the internal network; they first have to go through the proxy. A proxy server can be configured with firewall rules and other filtering workloads to put more weight into security.
4. Improve Security by Enforcing SSL Encryption.
Secure Sockets Layer (SSL) is a protocol that encrypts traffic using certificates and exchanged public-private key pairs. An SSL proxy can be deployed in the perimeter of a network to ensure SSL encryption. The proxy acts as a transparent proxy performing the SSL encryption/un-encryption between a client and the server, without them being aware of its presence.
Encrypting requests with SSL ensures better network security. It prevents any middle-man from intercepting sensitive data and blocks malicious sites from being accessed from the network.
5. Lower traffic by caching and buffering.
A proxy may be used to cache websites or buffer information to make access to frequently visited sites or services much faster. Since the local proxy can cache (save) data from a single request, every single request from multiple clients to the same server stays local. The proxy will retrieve it from its own memory and send it back to the local user. Caching reduces latency exponentially and improves network performance. Caching with a Proxy Server is similar to what Content Delivery Networks (CDNs) do.
6. Content Gateway.
A proxy can be used to filter, shape, and accommodate content from the outside world. Companies can tailor what their employees have access to when working with the Internet internally from the office.
Additionally, reverse proxies take requests from the Internet and forward them to the internal network. Reverse proxies can be used to protect web servers or customize the site to local (or global) users by tailoring the right content (such as translations or streaming media).
7. Monitoring and Logging Internet Access.
The Internet is an excellent resource for research, communications, data processing, and many mission-critical applications for any business. But unfortunately, the Internet also comes with many distractions and even harmful activities for the company. Network managers in a company can grant access to the Internet but limit and keep track of these activities that put the company at risk and lowers employee’s productivity.
The proxy may filter and log when employees access certain websites or services, such as social media, pornography, or videogames.
8. Avoiding the Blind Spot.
When companies want their employees to prioritize their Internet access resources for mission-critical activities, employees can still encrypt their data (which can be useful or harmful depending on the context). Network administrators cannot determine if the data (which is encrypted) being sent over the Internet is the company’s property, non-mission-critical, critical, or even malicious data. This blind spot (usually created with VPNs coming from inside organizations) puts a risk on the internal networks and violates the Internet’s usage policies.
9. Web Scraping for Market Research.
An excellent method to gather data to make a full market analysis is web scraping. A business may scrape anything from contact information, competitor prices, flight data, real estate listings, and the list goes on. Unfortunately, gathering or mining data from websites will ultimately get your IP blocked. Scraping needs to be scalable and undetectable. It needs to come from many IPs so that it becomes undetectable, fast, and anonymous.
A residential proxy IPv6 will not be blocked because it does not share a sub-network and has countless IPs (multiple proxies).
10. Search Engine Optimization (SEO) audits.
Modern SEO services such as Ahrefs, Moz, and Semrush use a combination of SEO keyword/ranking tracker scripts and lots of SEO proxies to scrape data (especially from Google). While doing an SEO audit (on your site or your competitor’s), you’ll need to scrape and crawl data from the site. Scraping and crawling web data from a site will directly have your IP blocked by (or clocked by your competition).
Use an SEO proxy to perform daily SEO audits, such as analyzing SERPs, researching the competition, finding keywords, monitoring competition rankings, and more— without getting your IP blocked. An SEO proxy will hide the real source from the original IP addresses.





Add Comment